Similar to how every individual has a unique set of loops, whorls, and arches on their physical fingerprints, the web browser you use to browse the internet leaves a distinct impression. However, instead of physical markers, browsers have their own personalized traits such as screen resolution, stored WebGL, and graphics card configurations. Similar to physical fingerprints, these browser fingerprints can be tracked as they navigate the internet, regardless of whether cookies are cleared or not.
When running multiple accounts, it's not as simple as changing your IP address and creating a new browser profile to get a new fingerprint. That's why in this article, XProxy will help you understand what a browser fingerprint is and how different platforms can recognize the unique fingerprint of each account. With this knowledge, you'll be better equipped to ensure the security and success of your multiple accounts.
Assessing the unique configuration of web browsers that connect to a web domain is a process called device fingerprinting. The fingerprint being scrutinized is made up of more than just the web browsing program. It includes attributes such as installed languages, operating system, plugins, and in-browser time zone, among others. Together, these attributes form a highly unique identifier that can be used to both verify a returning user and identify suspicious setups associated with fraud. For example, browser fingerprinting may be able to detect when users rely on emulators or spoofing tools, which could increase suspicion about their intentions on your website.
Most browser fingerprints are unique, and two users with the same fingerprint are almost certainly the same user on the same device. However, there is a small chance that multiple users connecting via mobile may have the exact same browser fingerprint, as people are less likely to make granular adjustments to their mobile browser settings. For this reason, device fingerprints should not be used as an identifying tool in isolation, and should be paired with other identifying data from the user to form a more reliable and holistic profile.
Browser fingerprinting tools gather user data relating to users’ software and hardware configurations, including:
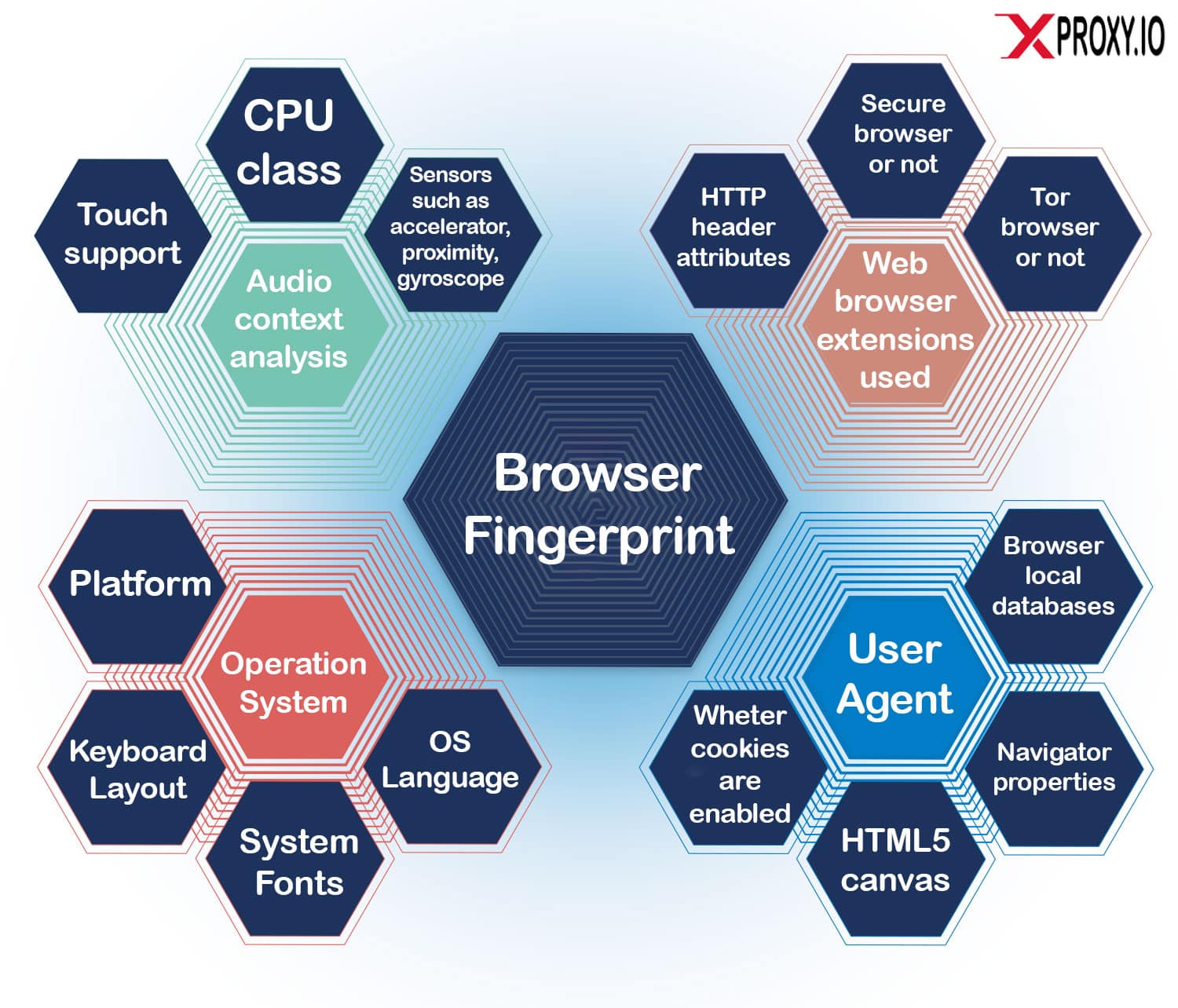
The above shows just how many parameters are taken into account to create a browser fingerprint.
Browser fingerprinting is a methodical process that silently collects and compiles numerous attributes of a browser setup and combines them into a single hash for identification. While every attribute is important to develop a unique identifying profile of a user, some are more closely associated with fraud than others. For instance, using a browser specifically designed to circumvent fraud prevention platforms is a common red flag.
Other data points within a browser fingerprint that may indicate fraud include:
If a browser configuration exhibits any of these unusual attributes, it may be assigned a higher risk score. However, it's essential to note that some users may have specific preferences that deviate from the norm, so very unusual configurations should be analyzed carefully.
Browser fingerprinting is usually accomplished by utilizing a small piece of JavaScript code that gathers information that is automatically sent during the connection process. This data includes details that are openly shared as part of the connection process, such as user-agent strings and HTTP headers that contain data about the browser type, version, and operating system. Additionally, installed browser plugins can also provide further data points about the user. Other data that can be collected includes screen settings, time zones, and languages.
By combining all of these data points, a comprehensive profile of the user is created, which is referred to as a browser fingerprint. To ensure privacy, the fingerprint is anonymized by being assigned a hash, which removes any identifying personal data from the profile while still providing a unique identifier. This identifier remains the same as long as the user connects from the same device, even if cookies are cleared. If any changes are detected in the fingerprint, the software may prompt for a manual review to verify that it is indeed the same user on a new device and not an instance of mulitple accounts.
Browser hashing generates an ID by looking at all browser fingerprint data points such as the user agent, operating system, windows, screen, font settings and more.
A new ID is created with each browser session.
The ID is created based on hardware data such as the device type, HTML5 canvas, whether it allows touch support, and more.
By combining all three hashes - browser, device, and cookie - you can gain a more comprehensive understanding of your users. In the past, legacy fraud detection methods only focused on the cookie hash or user agent, but modern fraudsters have become too clever to be caught through those means alone. Therefore, it's important to utilize all available information to stay ahead of potential fraud attempts.

Browser fingerprinting is a process that uses different tools to get similar results. Let's explore the standard features and see how platforms detect if you're running multiple accounts.
All data from online fingerprinting goes through a hash function. This turns data into fixed-sized values, making it easier to log, encrypt, analyze, and compare.
HTML5 websites have an element called the canvas, which generates data such as font size and active background color. This data creates a unique user ID for tracking, making it the most powerful feature of browser fingerprinting.
HTML5 canvas fingerprinting detects installed client fonts, browser font size, active background color, graphics card, and operating system, among others. This technique is used to prevent fraud because the same canvas image may appear differently on different computers.
WebGL is a JavaScript API that renders on-screen images and graphics, just like the canvas element. An image with a fixed size is rendered, and the technique estimates the type of graphics card the user has installed.
WebGL fingerprinting detects graphics card model and screen resolution.
A user agent, or UA, identifies a browser with a website. It's a string that, when detected by a site, can display tailored content for specific browsers.
User agent detection reveals browser name, version, or version number. Although web developers use user-agent switching tools to visualize how a site looks on different devices, fraudsters use the same type of tool to spoof a browser.
Audio fingerprinting is a technique that uses the AudioContext API to send low-frequency sound through a browser to a device. It measures how the device processes that data to help inform how to process audio. No audio is recorded, collected, or played, so microphone and speaker access are not necessary.
Audio fingerprinting detects AudioBuffer value and DynamicsCompressor value.
Companies that create mobile apps for smartphone OS can use a specific SDK to get extra information about devices.
Mobile device fingerprinting detects MAC address, serial number (Android only), device time zone, battery health, and CPU details.
By default, Tor makes each user have the exact same fingerprint. This ensures companies lack Tor fingerprinting information, ultimately providing fraudsters anonymity from basic anti-fraud solutions.
However, Tor detection works by running a test to see if the user's IP matches a known Tor exit node, thus determining whether a user is running Tor. While a Tor user might not have any malicious intent, Tor users should be flagged as high risk by default due to the statistically higher likelihood of fraudulent activity.
Selenium is an open-source tool that automates browsers, originally intended to help with web application testing. However, it's also the tool of choice for malicious actors who want to scrape your website, like ticket scalpers.
Although Selenium itself is difficult to detect, you can use JavaScript to check for evidence of WebDriver, the technology behind it. Our upcoming rule update will automatically flag browsers that are automated as risky, allowing you to block bot traffic and service abuse.
If you want to run multiple accounts, it's important to make sure your browser's IP and fingerprint are unique. One way to achieve this is by using XProxy, which allows you to generate an unlimited number of IPs using the mobile network. Another important step is to create a unique fingerprint for each account. To do this, you can use anti-detect browser software such as:
We wish you the best of luck!